How to hack wifi in kali linux
When it comes to hacking, wifi hacking is one of the most popular topic, because everyone wants a free internet connection. Many Hacking tools, software and techniques have been used by many hackers that crack a high secured Wi-Fi Network.
Kali linux is one of them, many people get confused, kali linux is not a cracking software instead it is a toolbox.
Note: Kali linux is tool kit, to hack wifi you have to choose right one. If one method don't work for you try another. I will cover all available tools in my upcoming posts.
Before hacking wifi, you must be aware of encryption technique used in order to secure wifi. It’s not only for knowledge although it will help you to choose different kind of suitable attack for different kind of encrypted networks.
There are different types of Encryption from which three basic security encryption are most common.
Wi-fi security: methods of encryption
These three methods of encryption has different types of vulnerability associated with wireless networks and can be hacked with different methods. The different types of Wireless Encryption Security techniques include the following (not deep details):
WEP:WEP is Wired Equivalent Privacy that can be cracked easily when configured appropriately. This method of encryption can be cracked within 5 minutes.
WPA:WPA is Wi-Fi Protected Access that provides strong security. Even then, there is possibility to crack if the Wi-Fi password if short. However, wireless networks can be hacked easily using various tools
WPA2:WPA2 is Wi-Fi Protected Access 2 that also eventually provides high security. You can hack this method of Wi-Fi encryption at the time of packet generation from Wi-Fi access points.
Techniques to hack wi-fi network
If you are much interested in hacking high security encryption based Wi-Fi networks, you need to arrange few things that are required at the time of Hacking process. After arranging all the essential things, you can hack a Wi-Fi network using few tools and techniques that can be seen below:
REQUIREMENTS
- Kali Linux OS
- External Wi-Fi Adapter or Inbuilt Wi-Fi Device
(Don't be confused, if your computer doesn’t have a wifi device, then you have to buy an external one).
METHOD 1: HACK Wi-Fi Network using Wifite
Wifite is a Linux-based platform tool that is available on variant Operating Systems like Kali, Backtrack 5, BlackBuntu, BackBox and Pentoo. Wifite is basically used to attack multiple encrypted networks (WEP, WPA/2 and WPS) in a row that is customized to be automated with only a few arguments.
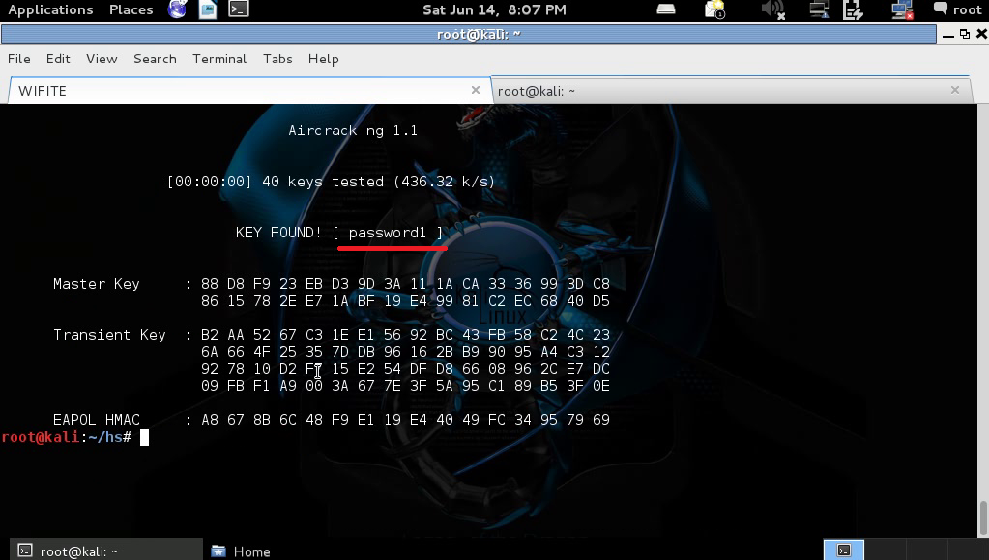
Simply type ‘wifite’ in terminal. Here, you can see List of Available Wi-Fi Access Points.
Wait for few seconds in order to notice nearby Wi-Fi points like WEP, WPA/WPA2.
Steps to Hack WEP Encryption based Wi-Fi Network
Step 1. Just choose the appropriate target NUM (1,2,3,..) in order to crack it.
Step 2. Make sure that the attack is completed within 10 minutes. You need not worry if one WEP WiFi attack fails, the other will come into action automatically for succeeding 10 minutes. Within few minutes the WEP Wi-Fi network gets hacked.
Step 3. You can see the WEP key that is present in the above image. It is a Hexadecimal representation of WEP WiFi’s password. That WEP Key can be used as the Wi-Fi password. You can also convert the Wi-Fi password into actual password using online Hex-to-ASCII converter.
Steps to Hack WPA Encryption based Wi-Fi Network
Hacking a Wi-Fi network that uses WPA security encryption is little bit tough when compared to WEP as this is highly protected encryption method. It takes less time to hack a Wi-Fi network that uses short passwords.
In order to hack this type of Wi-Fi network you need to use Handshake capture and wifite will capture it. I will post another method to capture Handshake file in my post.
Handshake Capture:
Handshake is a file that can be captured when Router and client(s) communicate to authenticate each other. You may have a doubt that, “What is the purpose of this Handshake file?” The main target is to hack Wi-Fi network. This Handshake file contain Wi-Fi password but in encrypted form. To get that password we need to perform different kinds of attack on Handshake file.
Following attack can be done on Handshake file.
Brute-Forcing: As the password is in encrypted form, let us try some other password combination on the encrypted password to acquire the original password. This process is known as Brute Forcing that is done offline. By using Brute-Forcing, the password present in the handshake file can be captured easily within few minutes.
Dictionary File: In the below image, you can see dictionary which is a file that contains all known words from various sources usually phrased as Wi-Fi password.
As soon as you start WPA handshake capture, it displays a message as “Client Found”. It generates a command using handshake capture (that contains password) as (TEST_C0-A0-BB-04-5C-A9.cap). The above command cracks the password file that must be saved at /root/DICTIONARY/. Till now, you have used two WPA attacks that are completed successfully.
A password file usually contains words that are created using combination of different characters, numbers and special symbols. A password requires a lot of computational power if it a strong password including numbers and other special characters. The above WPA Wi-Fi Security Encryption got cracked easily because of easy password. Suppose, if you are but dealing with strong password, it might take more hours to crack the password.
METHOD 2: HACK Wi-Fi Network using WIFIPHISHER
Wifiphisher is a security tool that performs one kind of phishing attacks which are against WPA networks. Unlike other methods of hacking, Wifiphisher is a type of social engineering attack that does not include brute forcing.
Wifiphisher is a tool that is used to hack a Wi-FI network and this attack makes use of three phases:
PHASE 1: Victim is being deauthenticated from their access point.
Wifiphisher tries to jam all the target access point’s wifi devices continuously that are available within range by sending deauth packets to the client from the access point.
Then it starts generating fake access points by copying an access point from a set of access points shown below:
PHASE 2:
This is the second phase where the Victim joins our fake access point.
It asks for password authentication.
Wifiphisher sniffs the area and copies the target access point’s settings.
Now, this tool creates a fake wireless access point that is modeled on the target by setting a NAT/DHCP server and forwards the right ports.
Consequently, because of the jamming, clients will start connecting to the fake access point. After this phase, the victim is Mitimed.
PHASE 3:
Victim is being served a realistic router config-looking page where the Wifiphisher tool employs a minimal web server that responds to HTTP & HTTPS requests.
As soon as the victim requests a page from the Internet, wifiphisher responds with a realistic fake page that asks for WPA password confirmation due to a router firmware upgrade.
Step by step hacking tutorials are coming…